
Photo by Glenn Carstens-Peters on Unsplash
How to spot and protect yourself against email phishing
Protecting yourself and data in this digital jungle
Table of contents
No headings in the article.
In this blog post , we are going to look at the various to protect yourself against email phishing. but first it is important to understand what is phishing.
 Phishing(pronounced: fishing) according to Microsoft is an attack that attempts to steal your money, your identity or your information, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate.
Phishing(pronounced: fishing) according to Microsoft is an attack that attempts to steal your money, your identity or your information, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate.
Like the tips above, this method isn’t foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.) These attackers use the guise of trusted institutions such schools, banks, software providers, music streaming platforms or any trusted online source to reveal sensitive information by clicking on a link to website. from there you are led to reveal sensitive personal information like your pin, password etc.
Common Examples of phishing emails
Typically phishing emails will ask for personal information, they might have generic greetings or lack of greetings, misspellings, unofficial "from" email addresses, unfamiliar webpages, and misleading hyperlinks. below are some examples of phishing emails to lookout for
- Company request for your sensitive information via email if you have ever received an unrequested email from an organization providing a link in their email that asks you to provide your sensitive information, it might be a phishing email. this is because most credible organizations will not ask you for your password, pin, credit score, credit card information via email.
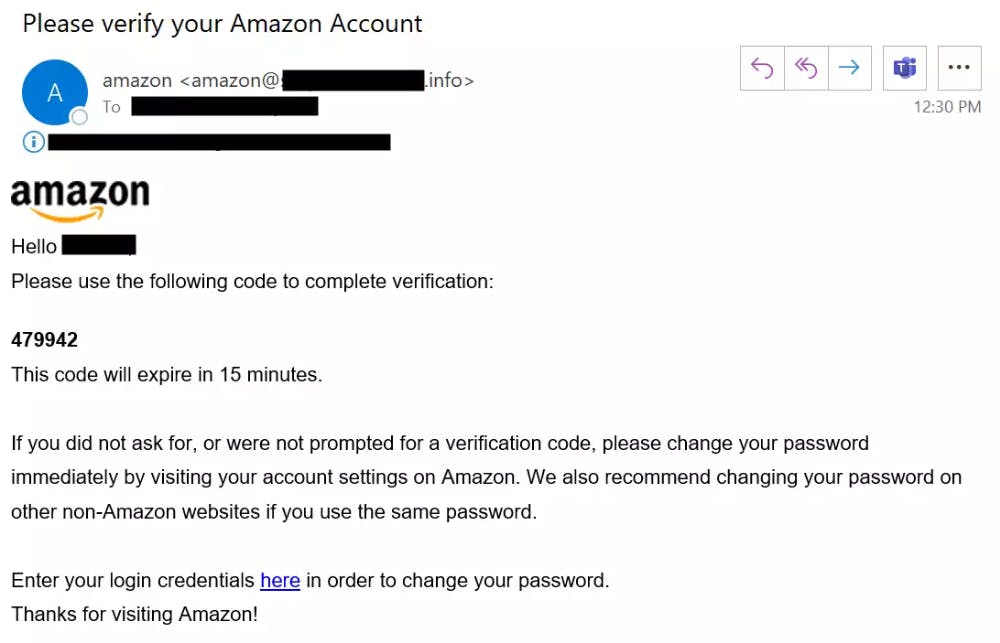
The organization doesn't have a domain name it is important to check the domain name of the entity sending you the email as it is clarifying that the name is correct too. to verify this, hover your mouse over the "from" address of the sender. Be on the lookout for any unusual additions like numbers or letters. this might not be a foolproof method but goes a long way in ensuring you are one step safer from phishing attacks.
Organizations sending unrequested attachments Unrequested emails that include attachment are a classic signature of scammers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website. In some companies that already have your email will send you information, such as a white paper, that may require a download. In that case, watch out for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)
How to protect yourself from phishing attacks
- Protect your computer by using security software. Set the software to update automatically so it can deal with any new security threats.

Protect your mobile phone by setting software to update automatically. These updates could give you critical protection against a lot of security threats.
Protect your accounts by using the multi-factor authentication. Some websites or accounts offer extra security by requiring two or more credentials to log in to your account. This is called multi-factor authentication.

The additional credentials you need to log in to your account fall into two categories:
Something you have — like a passcode you get via an authentication app or a security key. Something you are — like a scan of your fingerprint, your retina, or your face. Multi-factor authentication makes it harder for scammers to log in to your accounts if they do get your username and password.
- Protect your data by backing it up. it is very important to back up your data and make sure those backups aren’t connected to your home network. You can copy your computer files to an external hard drive or cloud storage ideally. Do back up the data on your phone as well.


